一、容器镜像仓库Harbor部署
1.1 在docker主机部署harbor
1.1.1 docker-ce安装
使用阿里云开源软件镜像站。
# step 1: 安装必要的一些系统工具
sudo yum install -y yum-utils device-mapper-persistent-data lvm2
# Step 2: 添加软件源信息
sudo yum-config-manager --add-repo https://mirrors.aliyun.com/docker-ce/linux/centos/docker-ce.repo
# Step 3
sudo sed -i 's+download.docker.com+mirrors.aliyun.com/docker-ce+' /etc/yum.repos.d/docker-ce.repo
# Step 4: 更新并安装Docker-CE
sudo yum makecache fast
sudo yum -y install docker-ce
# Step 4: 开启Docker服务
sudo systemctl start docker
# 注意:
# 官方软件源默认启用了最新的软件,您可以通过编辑软件源的方式获取各个版本的软件包。例如官方并没有将测试版本的软件源置为可用,您可以通过以下方式开启。同理可以开启各种测试版本等。
# vim /etc/yum.repos.d/docker-ce.repo
# 将[docker-ce-test]下方的enabled=0修改为enabled=1
#
# 安装指定版本的Docker-CE:
# Step 1: 查找Docker-CE的版本:
# yum list docker-ce.x86_64 --showduplicates | sort -r
# Loading mirror speeds from cached hostfile
# Loaded plugins: branch, fastestmirror, langpacks
# docker-ce.x86_64 17.03.1.ce-1.el7.centos docker-ce-stable
# docker-ce.x86_64 17.03.1.ce-1.el7.centos @docker-ce-stable
# docker-ce.x86_64 17.03.0.ce-1.el7.centos docker-ce-stable
# Available Packages
# Step2: 安装指定版本的Docker-CE: (VERSION例如上面的17.03.0.ce.1-1.el7.centos)
# sudo yum -y install docker-ce-[VERSION]
1.1.2 docker compose安装
- 下载最新版本:
sudo curl -L "https://github.com/docker/compose/releases/latest/download/docker-compose-$(uname -s)-$(uname -m)" -o /usr/local/bin/docker-compose - 赋予可执行权限给下载的二进制文件:
sudo chmod +x /usr/local/bin/docker-compose - 验证安装是否成功。运行以下命令,查看Docker Compose版本信息:
docker-compose --version
1.1.3 获取harbor安装文件
- 前往 harbor 的github仓库下载安装文件
https://github.com/goharbor/harbor/releases,下载最新稳定版
- 选择离线安装包
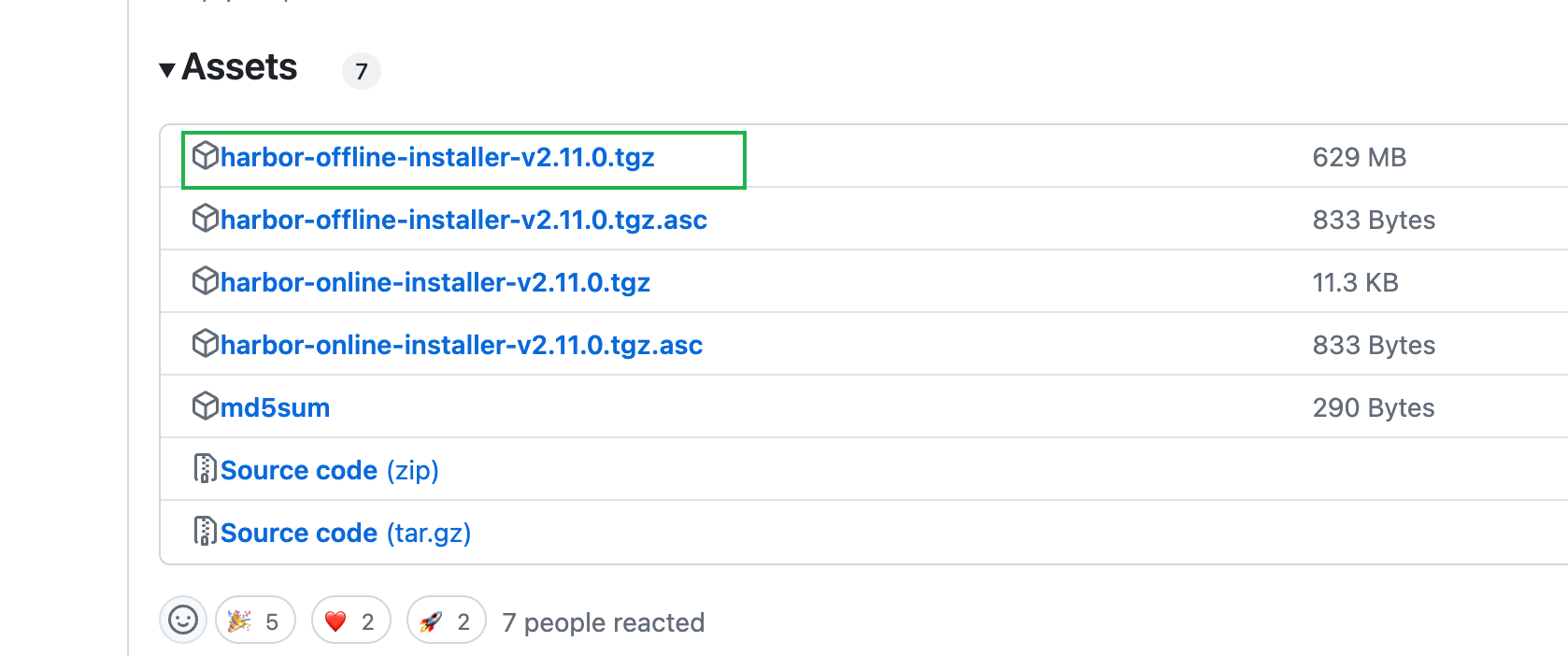
- 下载harbor离线安装包
$ wget https://github.com/goharbor/harbor/releases/download/v2.11.0/harbor-offline-installer-v2.11.0.tgz
$ ls
harbor-offline-installer-v2.11.0.tgz
1.1.4 修改配置文件
- 解压harbor离线安装包
$ tar zxf harbor-offline-installer-v2.11.0.tgz
$ ls
$ ls harbor
common.sh harbor.v2.11.0.tar.gz harbor.yml.tmpl install.sh LICENSE prepare
- 由模板创建配置文件并修改
$ cd harbor/
$ cp harbor.yml.tmpl harbor.yml
$ vim harbor.yml
# Configuration file of Harbor
# The IP address or hostname to access admin UI and registry service.
# DO NOT use localhost or 127.0.0.1, because Harbor needs to be accessed by external clients.
hostname: hub.17ker.top
# http related config
http:
# port for http, default is 80. If https enabled, this port will redirect to https port
port: 80
# https related config
https:
# https port for harbor, default is 443
port: 443
# The path of cert and key files for nginx
certificate: /opt/harbor/ssl/star.17ker.top.crt
private_key: /opt/harbor/ssl/star.17ker.top.key
# enable strong ssl ciphers (default: false)
# strong_ssl_ciphers: false
...
# The initial password of Harbor admin
# It only works in first time to install harbor
# Remember Change the admin password from UI after launching Harbor.
harbor_admin_password: Harbor12345 #访问密码
...
1.1.5 执行预备脚本
$ sudo ./prepare
prepare base dir is set to /opt/harbor
Unable to find image 'goharbor/prepare:v2.11.0' locally #本地没有,需下载镜像
v2.11.0: Pulling from goharbor/prepare
Generated configuration file: /config/portal/nginx.conf
Generated configuration file: /config/log/logrotate.conf
Generated configuration file: /config/log/rsyslog_docker.conf
Generated configuration file: /config/nginx/nginx.conf
Generated configuration file: /config/core/env
Generated configuration file: /config/core/app.conf
Generated configuration file: /config/registry/config.yml
Generated configuration file: /config/registryctl/env
Generated configuration file: /config/registryctl/config.yml
Generated configuration file: /config/db/env
Generated configuration file: /config/jobservice/env
Generated configuration file: /config/jobservice/config.yml
Generated and saved secret to file: /data/secret/keys/secretkey
Successfully called func: create_root_cert
Generated configuration file: /compose_location/docker-compose.yml
Clean up the input dir
1.1.6 执行安装脚本
$ sudo ./install.sh
[Step 0]: checking if docker is installed ...
Note: docker version: 26.1.3
[Step 1]: checking docker-compose is installed ...
Note: Docker Compose version v2.27.0
[Step 2]: loading Harbor images ...
[Step 3]: preparing environment ...
[Step 4]: preparing harbor configs ...
prepare base dir is set to /opt/harbor
[Step 5]: starting Harbor ...
[+] Running 10/10
✔ Network harbor_harbor Created 0.1s
✔ Container harbor-log Started 0.3s
✔ Container redis Started 0.6s
✔ Container harbor-db Started 0.7s
✔ Container harbor-portal Started 0.7s
✔ Container registry Started 0.6s
✔ Container registryctl Started 0.7s
✔ Container harbor-core Started 0.9s
✔ Container nginx Started 1.2s
✔ Container harbor-jobservice Started 1.1s
✔ ----Harbor has been installed and started successfully.----
1.1.7 验证运行情况
# docker ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
71c0db683e4a goharbor/nginx-photon:v2.5.1 "nginx -g 'daemon of…" About a minute ago Up About a minute (healthy) 0.0.0.0:80->8080/tcp, :::80->8080/tcp, 0.0.0.0:443->8443/tcp, :::443->8443/tcp nginx
4e3b53a86f01 goharbor/harbor-jobservice:v2.5.1 "/harbor/entrypoint.…" About a minute ago Up About a minute (healthy) harbor-jobservice
df76e1eabbf7 goharbor/harbor-core:v2.5.1 "/harbor/entrypoint.…" About a minute ago Up About a minute (healthy) harbor-core
eeb4d224dfc4 goharbor/harbor-portal:v2.5.1 "nginx -g 'daemon of…" About a minute ago Up About a minute (healthy) harbor-portal
70e162c38b59 goharbor/redis-photon:v2.5.1 "redis-server /etc/r…" About a minute ago Up About a minute (healthy) redis
8bcc0e9b06ec goharbor/harbor-registryctl:v2.5.1 "/home/harbor/start.…" About a minute ago Up About a minute (healthy) registryctl
d88196398df7 goharbor/registry-photon:v2.5.1 "/home/harbor/entryp…" About a minute ago Up About a minute (healthy) registry
ed5ba2ba9c82 goharbor/harbor-db:v2.5.1 "/docker-entrypoint.…" About a minute ago Up About a minute (healthy) harbor-db
dcb4b57c7542 goharbor/harbor-log:v2.5.1 "/bin/sh -c /usr/loc…" About a minute ago Up About a minute (healthy) 127.0.0.1:1514->10514/tcp harbor-log
1.1.8 访问harbor UI界面
1.2 在kubernetes集群中部署harbor
由于涉及后面技术内容,例如: pv、pvc、helm等,后期内容做介绍。
二、Kubernetes集群使用harbor仓库
2.1 通过secret使用harbor仓库
2.1.1 新建一个harbor私有仓库
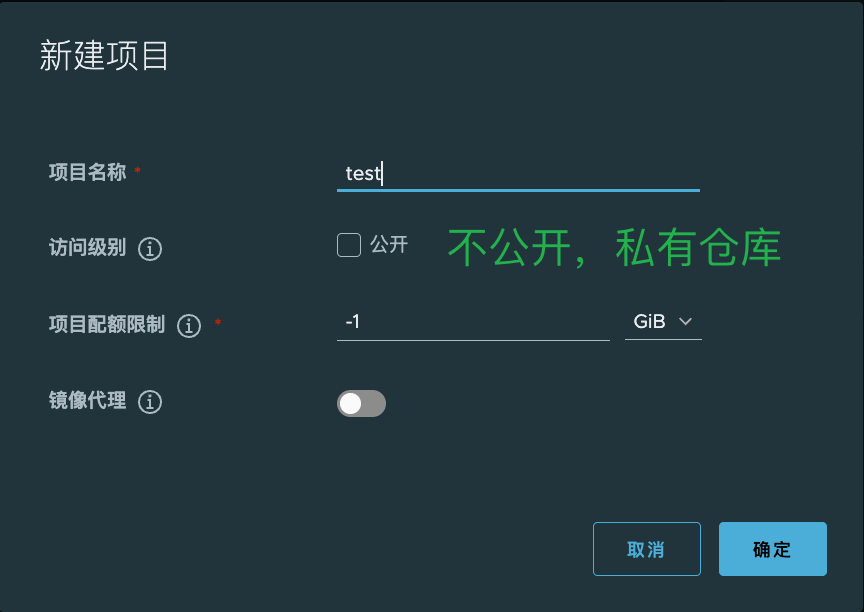
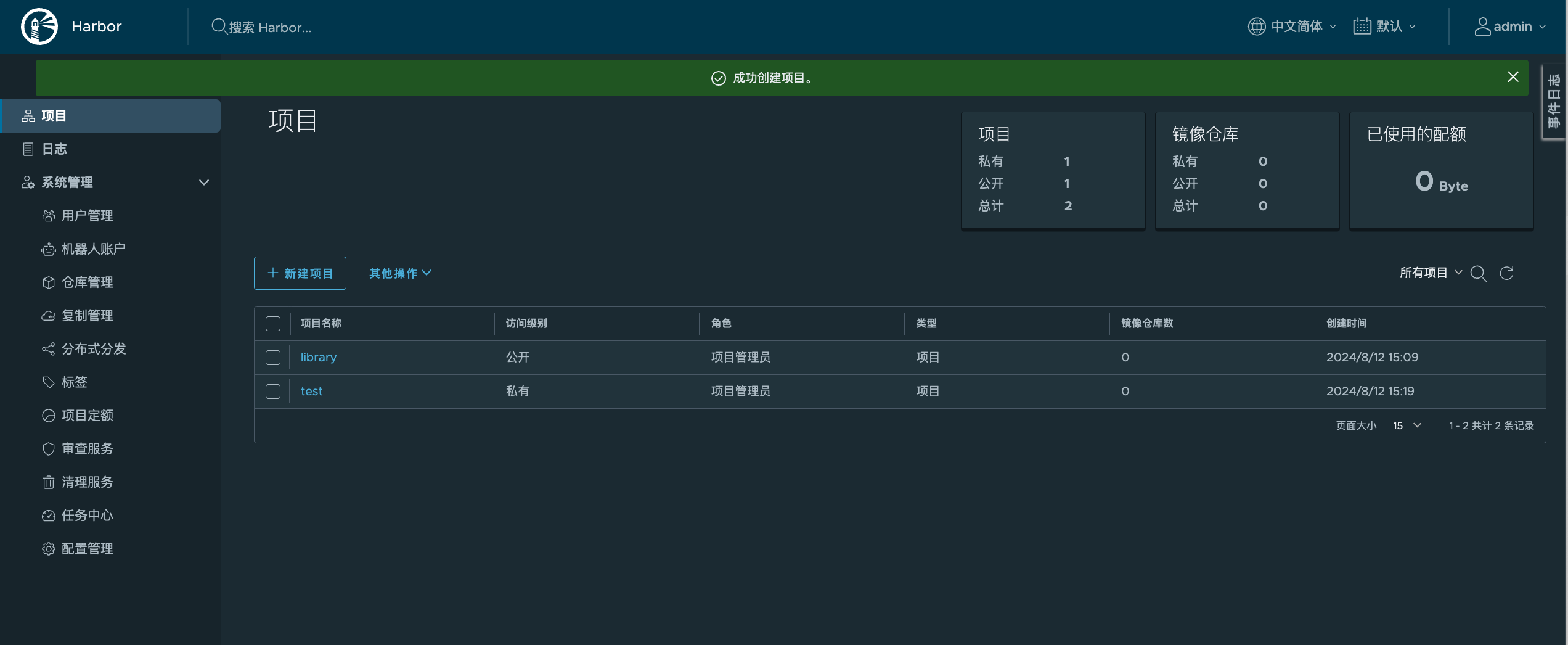
2.1.2 上传nginx测试镜像到harbor
- docker-cli 登录 hub.17ker.top
$ docker login hub.17ker.top Username: admin Password: #输入不显示 Harbor12345 WARNING! Your password will be stored unencrypted in ~/.docker/config.json. Configure a credential helper to remove this warning. See https://docs.docker.com/engine/reference/commandline/login/#credentials-store Login Succeeded - 下载nginx镜像,上传到私有仓库
$ docker pull nginx:1.19.0-alpine $ docker tag nginx:1.19.0-alpine hub.17ker.top/test/nginx:1.19.0-alpine $ docker push hub.17ker.top/test/nginx:1.19.0-alpine - 仓库中已经出现对应的镜像
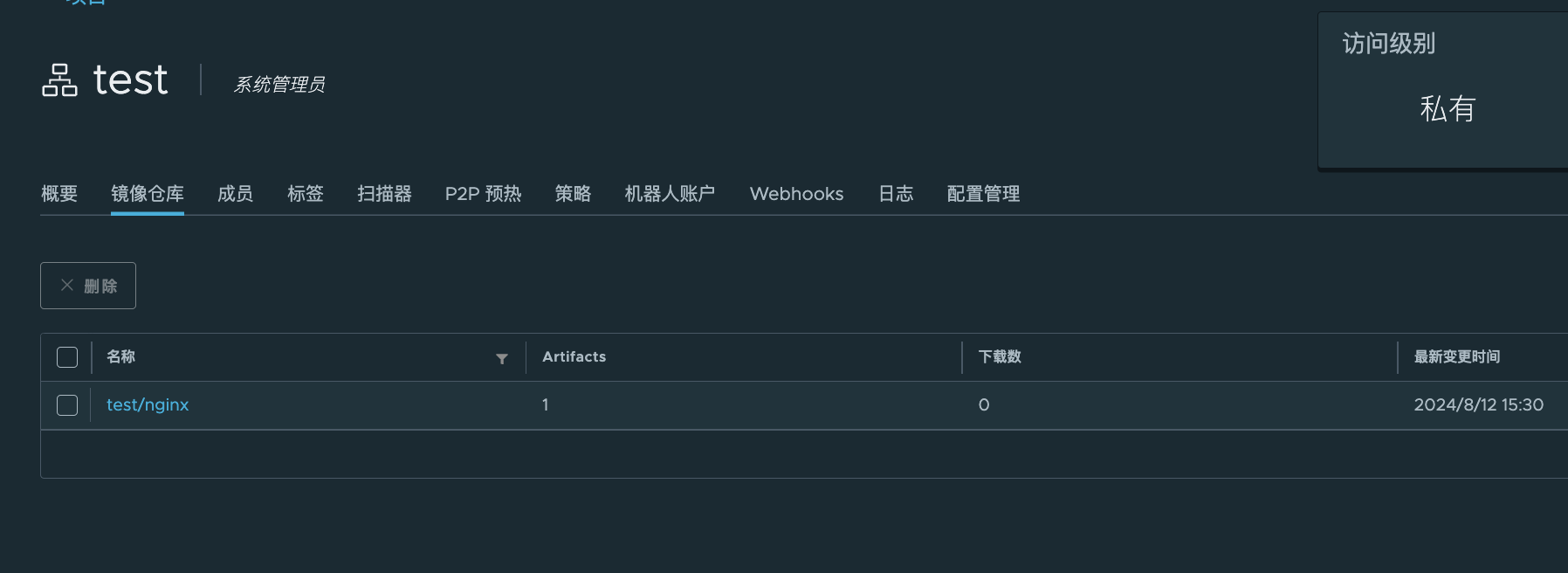
2.1.4 创建docker-registry类型secret
[root@k8s-master1 ~]# kubectl create secret docker-registry harbor-secret --docker-server=hub.17ker.top --docker-username=admin --docker-password=Harbor123456
说明:
- 类型为docker-registry
- --docker-server指定harbor仓库的IP
- --docker-username指定harbor仓库的登录用户名
- --docker-password指定harbor仓库的登录密码
验证查看
[root@k8s-master1 ~]# kubectl get secret |grep harbor-secret
harbor-secret kubernetes.io/dockerconfigjson 1 19s
[root@k8s-master1 ~]# kubectl describe secret harbor-secret
Name: harbor-secret
Namespace: default
Labels: <none>
Annotations: <none>
Type: kubernetes.io/dockerconfigjson
Data
====
.dockerconfigjson: 94 bytes
2.1.5 创建pod并使用secret
[root@k8s-master1 ~]# vim pod-harbor.yml
apiVersion: v1
kind: Pod
metadata:
name: pod-harbor
spec:
containers:
- name: c1
image: 192.168.10.250/test/nginx:v1
imagePullSecrets: # 定义镜像下载使用的secrets
- name: harbor-secret # 与上面的secret一致
[root@k8s-master1 ~]# kubectl apply -f pod-harbor.yml
pod/pod-harbor created
2.1.6 验证pod
[root@k8s-master1 ~]# kubectl describe pod pod-harbor
Events:
Type Reason Age From Message
---- ------ ---- ---- -------
Normal Scheduled 16s default-scheduler Successfully assigned default/pod-harbor to k8s-worker1
Normal Pulling 15s kubelet Pulling image "192.168.10.250/test/nginx:v1"
Normal Pulled 14s kubelet Successfully pulled image "192.168.10.250/test/nginx:v1" in 630.869309ms
Normal Created 14s kubelet Created container c1
Normal Started 14s kubelet Started container c1
可以看到是从192.168.10.250/test/nginx:v1拉取的镜像
2.2 通过serviceaccout使用harbor仓库
2.2.1 设为serviceaccount默认规则
如果每次编写yaml文件都需要添加imagePullSecrets这2行配置,有点麻烦, 有没有在不需要添加这2行配置就可以实现下载harbor仓库里面的镜像呢?答案是有的,可以把secret配置到serviceAccount中即可。
2.2.2 创建serviceaccount及应用过程
- 创建serviceaccount
[root@k8s-master1 ~]# vim serviceaccount-harbor-sa.yaml
apiVersion: v1
kind: ServiceAccount
metadata:
name: harbor-sa
namespace: default
[root@k8s-master1 ~]# kubectl apply -f serviceaccount-harbor-sa.yaml
serviceaccount/harbor-sa created
[root@k8s-master1 ~]# kubectl get sa |grep harbor-sa
harbor-sa 1 14s
2.修改serviceaccount添加使用harbor-secret
[root@k8s-master1 ~]# kubectl describe serviceaccount harbor-sa
Name: harbor-sa
Namespace: default
Labels: <none>
Annotations: <none>
Image pull secrets: <none>
Mountable secrets: harbor-sa-token-thxwq
Tokens: harbor-sa-token-thxwq
Events: <none>
[root@k8s-master1 ~]# kubectl patch serviceaccount harbor-sa -n default -p '{"imagePullSecrets": [{"name": "harbor-secret"}]}'
serviceaccount/harbor-sa patched
[root@k8s-master1 ~]# kubectl describe serviceaccount harbor-sa
Name: harbor-sa
Namespace: default
Labels: <none>
Annotations: <none>
Image pull secrets: harbor-secret
Mountable secrets: harbor-sa-token-thxwq
Tokens: harbor-sa-token-thxwq
Events: <none>
[root@k8s-master1 ~]# kubectl get serviceaccount harbor-sa -o yaml
apiVersion: v1
imagePullSecrets:
- name: harbor-secret # 确认,通过patch方式更新了
kind: ServiceAccount
......
3.修改yaml使用serviceAccount
[root@k8s-master1 ~]# vim pod-harbor.yml
apiVersion: v1
kind: Pod
metadata:
name: pod-harbor
spec:
serviceAccount: harbor-sa # 原来的2句换成使用harbor-sa这个serviceAccount
containers:
- name: c1
image: 192.168.122.18/test/nginx:v1
- 删除先前的重新创建pod验证
[root@k8s-master1 ~]# kubectl delete pod pod-harbor
pod "pod-harbor" deleted
[root@k8s-master1 ~]# kubectl apply -f pod-harbor.yml
pod/pod-harbor created
[root@k8s-master1 ~]# kubectl get pods
NAME READY STATUS RESTARTS AGE
pod-harbor 1/1 Running 0 8s
[root@k8s-master1 ~]# kubectl describe pods pod-harbor
Events:
Type Reason Age From Message
---- ------ ---- ---- -------
Normal Scheduled 13s default-scheduler Successfully assigned default/pod-harbor to k8s-worker2
Normal Pulling 13s kubelet Pulling image "192.168.10.250/test/nginx:v1"
Normal Pulled 12s kubelet Successfully pulled image "192.168.10.250/test/nginx:v1" in 731.788686ms
Normal Created 12s kubelet Created container c1
Normal Started 12s kubelet Started container c1
补充: serviceAccount可以实现不同namespace下载镜像使用访问harbor账号的不同。


评论区